Admin
Joined - December 2025
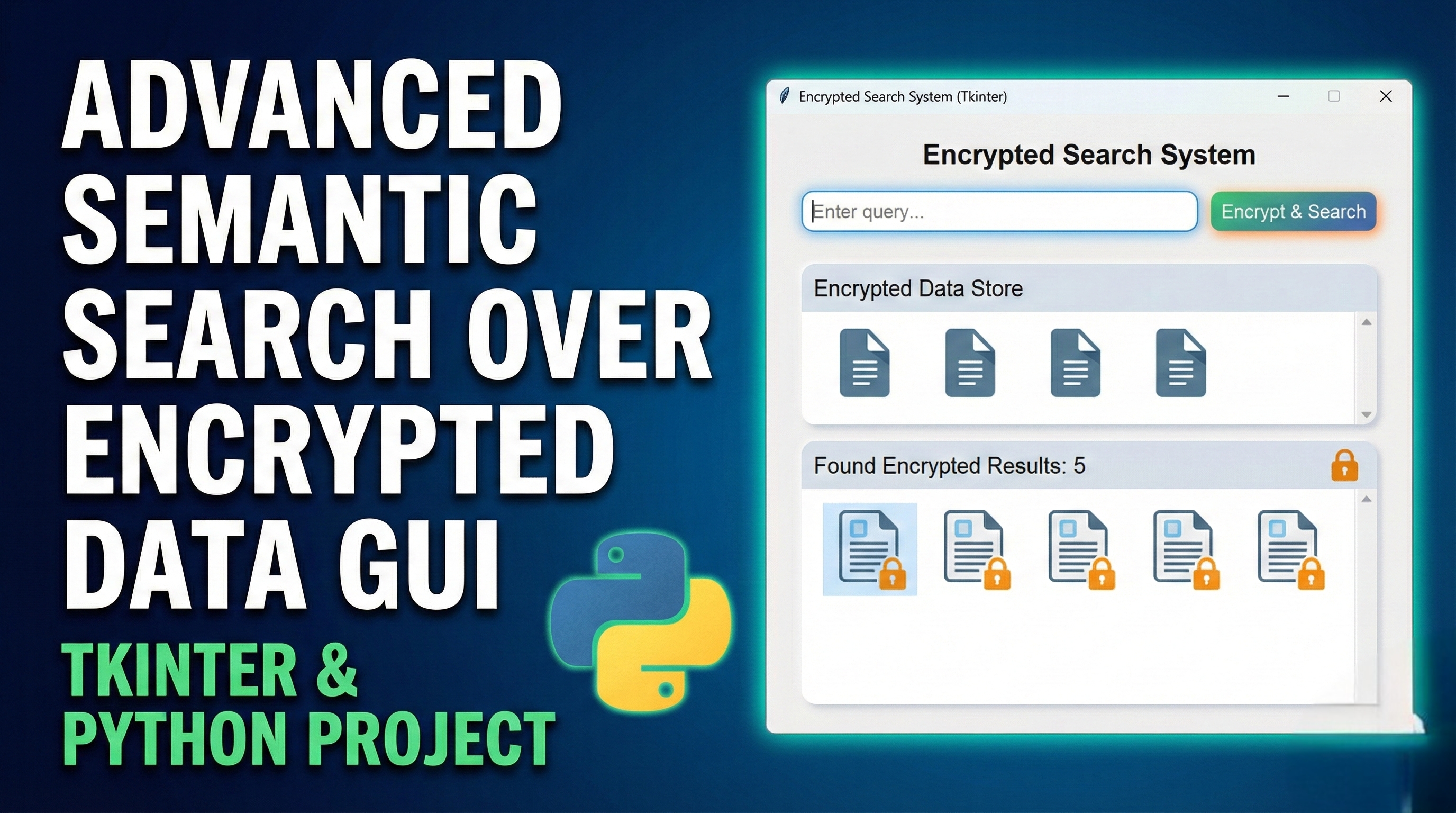
Key Features: 1. Encryption System
AES encryption using Fernet (symmetric encryption)
Password-based key derivation (PBKDF2)
Secure key management with save/load functionality
Real-time encryption status monitoring
2. Semantic Search Capabilities
TF-IDF vectorization for document representation
Cosine similarity for semantic matching
Adjustable semantic weight and similarity thresholds
Support for both encrypted and plaintext search
3. Advanced GUI Components
Modern tabbed interface
Treeview widgets for document management
Real-time search results display
Progress bars for long operations
Status bar with encryption status
4. Document Management
Add, update, delete documents
Import/export JSON functionality
Secure delete option (overwrites data)
Auto-encryption of new documents
5. Analytics Dashboard
Search statistics and metrics
Visualizations using Matplotlib
Real-time charts showing:
Top search results (bar chart)
Encryption status distribution (pie chart)
6. Security Features
Encrypted data storage
Secure password input
Key file management
Encryption event logging
7. Settings Configuration
Adjustable similarity thresholds
Performance settings
Security preferences
Search parameters
How to Use:
Start: Run the application
Setup Encryption: Go to Encryption tab, set password, generate keys
Add Documents: Go to Database tab, add documents (they auto-encrypt)
Search: Go to Search tab, enter query, adjust semantic weight if needed
Analyze: View search analytics in Analytics tab
Requirements:
bash
pip install tkinter scikit-learn cryptography matplotlib Security Notes:
This is a demonstration system - use stronger encryption in production
Always use strong, unique passwords
Store encryption keys securely
Consider adding multi-factor authentication for production use
Implement proper key rotation policies
Get the updates.
Up to Top
Comments