Admin
Joined - December 2025
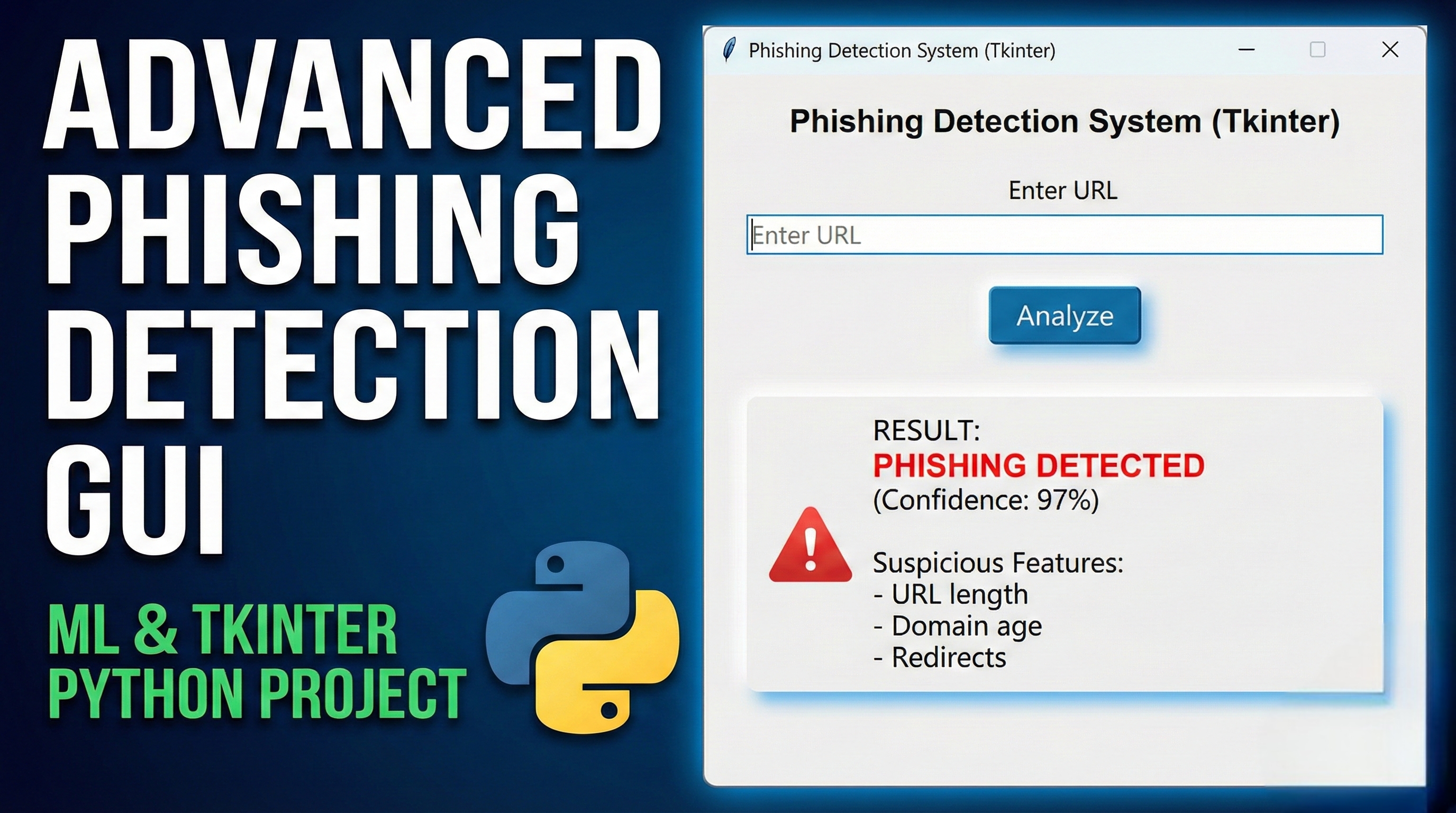
Features of this Advanced Phishing Detection System: 1. Modern GUI with Tkinter
Clean, professional interface with dark theme
Tabbed navigation for different functionalities
Progress indicators and visual feedback
Responsive design with scrollable areas
2. Machine Learning Integration
Random Forest classifier for phishing detection
Feature extraction from URLs (length, special characters, HTTPS, etc.)
Confidence scoring and probability distribution
Demo model with synthetic data (trainable on real data)
3. Core Functionalities
Single URL Analysis: Real-time phishing detection for individual URLs
Batch Analysis: Process multiple URLs at once
History Tracking: Maintain analysis history with timestamps
Model Information: Display details about the ML model
4. Advanced Features
Visual confidence meters and progress bars
Color-coded risk assessment (Red for phishing, Green for safe)
Feature analysis display showing extracted URL characteristics
Probability distribution visualization
5. User Experience
Threaded operations to prevent UI freezing
Status bar for real-time feedback
Error handling with user-friendly messages
Clear and intuitive controls
Installation Requirements:
Create a requirements.txt file:
text
scikit-learn==1.3.0 pandas==2.0.3 numpy==1.24.3 joblib==1.3.2 requests==2.31.0 python-whois==0.9.3 Usage Instructions:
Install dependencies:
bash
pip install -r requirements.txt
Run the application:
bash
python phishing_detector.py
To test:
Enter URLs in the "URL Analysis" tab
Use "Batch Analysis" for multiple URLs
Check "Model Info" for technical details
View "History" for past analyses
Sample Test URLs:
Try these for testing:
https://www.google.com (Legitimate)
http://secure-login-verify-account.com (Suspicious)
http://192.168.1.1/login.php (Suspicious - IP address)
https://www.paypal.com.secure.login.verify.account.com (Phishing attempt)
Note:
This is a demonstration system using synthetic data. For production use:
Train on real phishing datasets (like PhishTank)
Implement more sophisticated feature extraction
Add real-time WHOIS lookup
Include content analysis
Implement regular model updates
Get the updates.
Up to Top
Comments