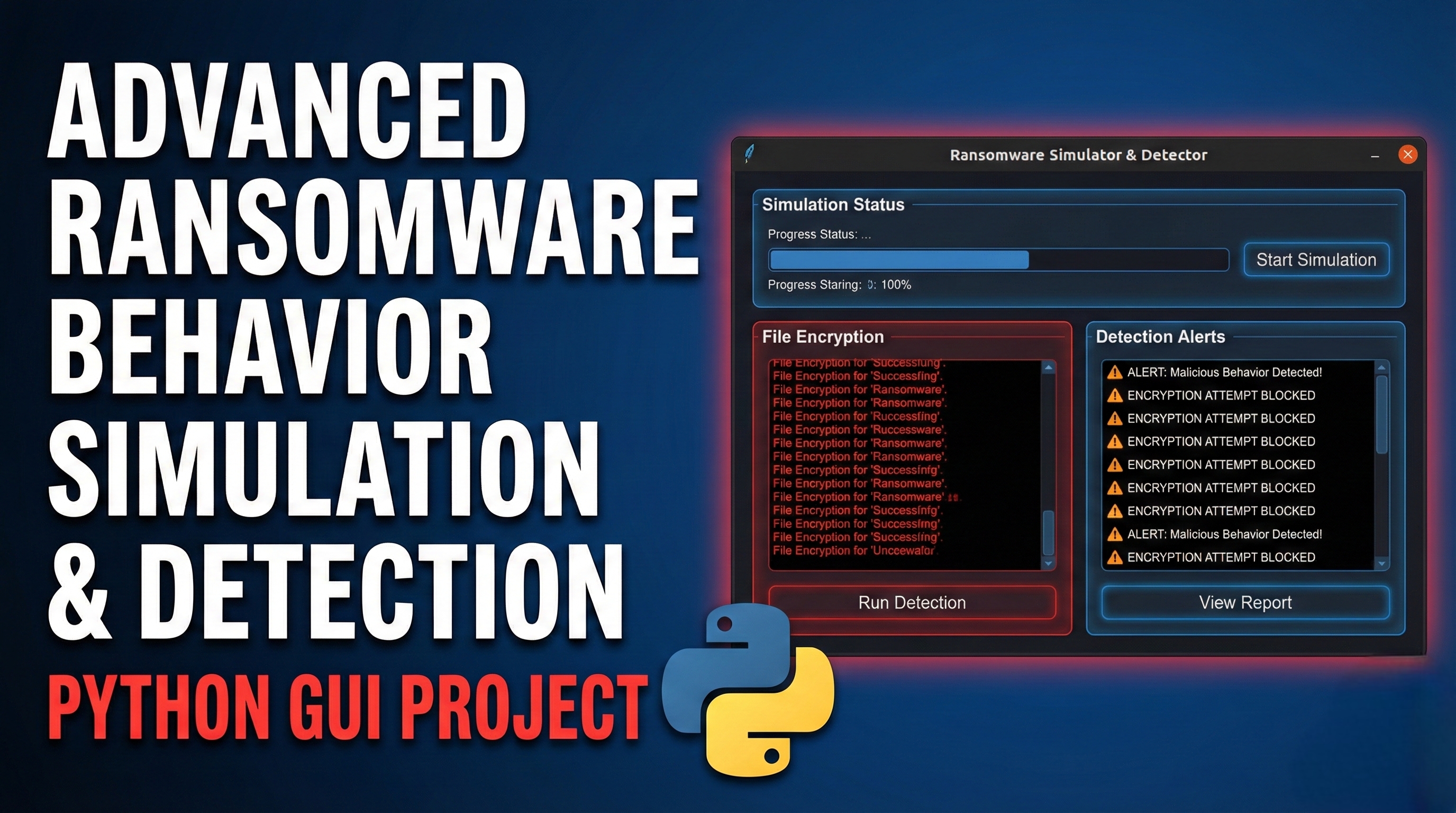
This advanced ransomware detection system includes:
Key Features:
1. Behavioral Analysis Engine
- Shannon entropy calculation for encrypted file detection
- Pattern recognition for suspicious activities
- Real-time scoring system (0-100)
- ML-inspired anomaly detection
2. Ransomware Simulation
- Controlled simulation with test file creation
- Multiple simulation speeds (slow/medium/fast)
- Mock encryption with .encrypted extensions
- Ransom note creation simulation
- Safe cleanup operations
3. Real-time Monitoring
- File system watcher for multiple directories
- Detection of suspicious extensions (.encrypted, .locked, .crypt)
- Rapid file modification detection
- Ransom note pattern matching
4. GUI Features
- Modern dark theme interface
- Real-time threat level display
- Suspicion score with progress bar
- Colored log viewer with filtering
- Statistics dashboard
- Thread-safe logging system
5. Detection Capabilities
- Rapid encryption detection (5 files/sec)
- Suspicious extension changes
- High entropy file identification
- Ransom note pattern matching
- Behavioral anomaly scoring
Installation Requirements:
bash
pip install pycryptodome psutil watchdog numpy
Usage Instructions:
- Setup Test Directory: Choose/create a directory for simulation
- Start Simulation: Simulate ransomware behavior to test detection
- Enable Monitoring: Monitor directories for real threats
- View Detection Log: See real-time alerts and analysis
- Monitor Threat Level: Watch suspicion score and threat level
Safety Features:
- All operations are contained within test directories
- No real encryption - only simulation for safety
- Easy cleanup of test files
- Clear warnings and confirmations
Detection Patterns:
- Rapid File Modifications: 10 files/second
- Suspicious Extensions: .encrypted, .locked, .crypt
- High Entropy Files: 0.95 normalized entropy
- Ransom Notes: README, DECRYPT, HOW_TO_RECOVER patterns
Comments